This is an old revision of the document!
Authentication Tab (Login Dialog)
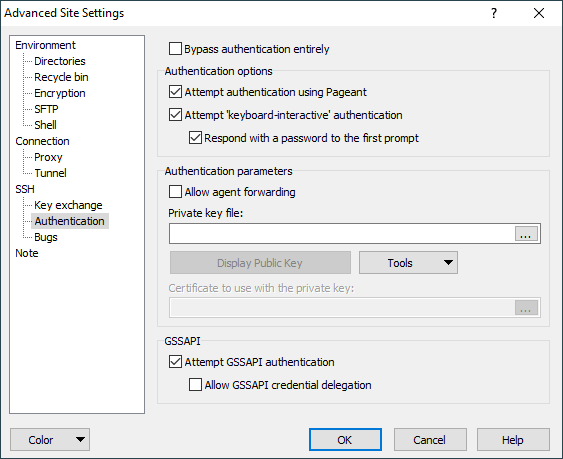
Authentication tab allows you to configure authentication options of SSH protocol.
Advertisement
- Attempt TIS or CryptoCard authentication
- Attempt keyboard-interactive authentication
- Attempt MIT Kerberos GSSAPI authentication
- Allow agent forwarding
Attempt TIS or CryptoCard authentication
TIS and CryptoCard authentication are simple challenge/response forms of authentication available in SSH protocol version 1 only. You might use them if you were using S/Key one-time passwords, for example, or if you had a physical security token that generated responses to authentication challenges.
With this switch enabled, WinSCP will attempt these forms of authentication if the server is willing to try them. You will be presented with a challenge string (which will be different every time) and must supply the correct response in order to log in. If your server supports this, you should talk to your system administrator about precisely what form these challenges and responses take.1
Attempt keyboard-interactive authentication
The SSH 2 equivalent of TIS authentication is called ‘keyboard-interactive’. It is a flexible authentication method using an arbitrary sequence of requests and responses; so it is not only useful for challenge/response mechanisms such as S/Key, but it can also be used for (for example) asking the user for a new password when the old one has expired.1
WinSCP leaves this option enabled by default, but supplies a switch to turn it off in case you should have trouble with it. If your servers uses keyboard-interactive authentication to ask for your password only, and you wish to allow WinSCP to reply with your stored password, tick Respond with password to the first prompt.
Advertisement
Attempt MIT Kerberos GSSAPI authentication
The switch tells WinSCP to attempt Kerberos authentication.
The GSSAPI is a generic API for doing client-server authentication. The motivation behind it is that every security system has its own API, and the effort involved with adding different security systems to applications is extremely difficult with the variance between security APIs. However, with a common API, application vendors could use the generic API and it could work with any number of security platforms (Kerberos, Entrust, …).
Currently, only MIT Kerberos 5 implementation of GSSAPI is supported.
The support of SSPI (Microsoft specific implementation of GSSAPI) is under development.
To use this authentication, you need to have Kerberos for Windows installed.
Allow agent forwarding
This option allows the SSH server to open forwarded connections back to your local copy of Pageant. If you are not running Pageant, this option will do nothing. Learn more about agent forwarding. 1
- The text is copy of PuTTY User Manual or was inspired by it.Back