@martin, I found out the core of the problem.
Really it was simple one.
You have certificate which was issued by custom CA (
Certificate Authority).
In this case as expected your Windows system doesn't have:
- Root certificate in "Trusted Root Certification Authorities" (I call it CA-ROOT);
- Intermediate certificate in "Intermediate Certification Authorities" (I call it CA-SUB) (SUB is from subordinate).
1. Error:
@sessionlog@
. 2017-02-06 15:38:00.824 Certificate failed to verify against Windows certificate store: Error: 800B0109, Chain index: 0, Element index: -1
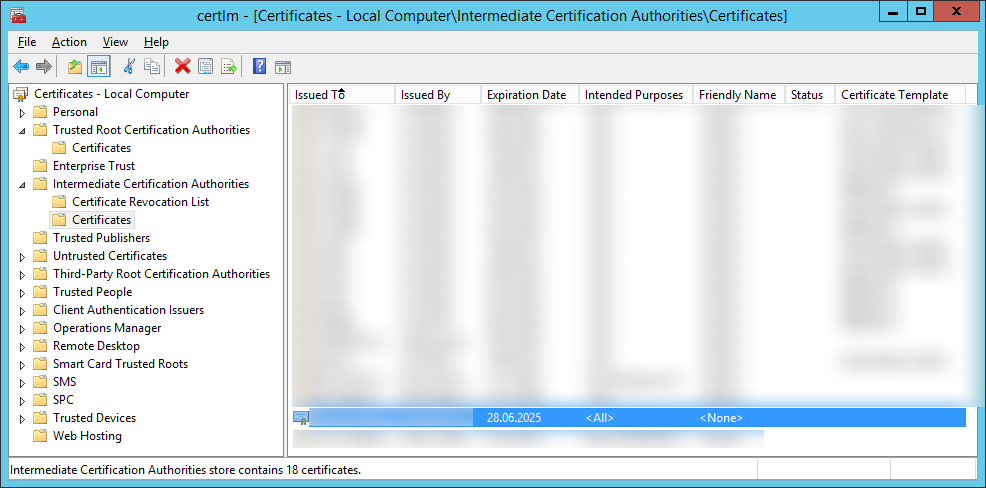
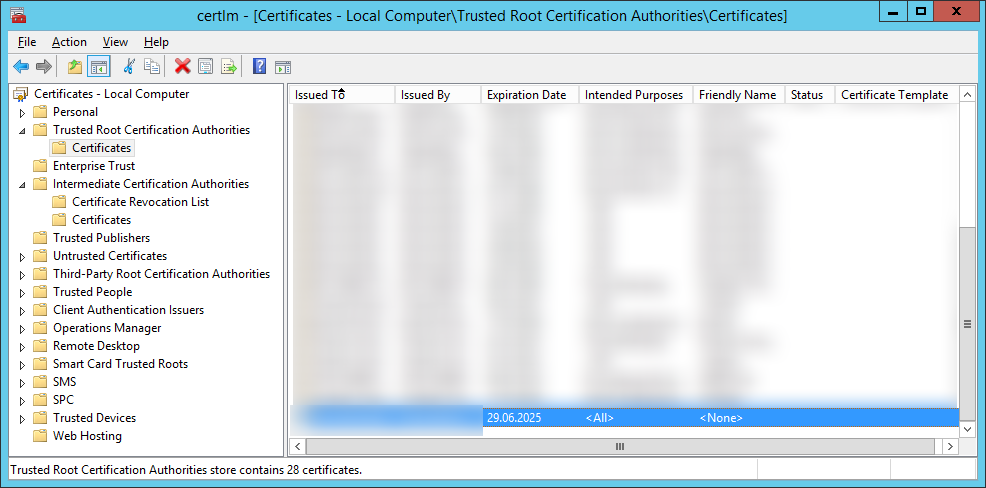
Add into Windows Storage "certlm - [Certificates - Local computer]" (see screenshot) certificates of your custom CA:
- Root certificate in "Trusted Root Certification Authorities";
- Intermediate certificate in "Intermediate Certification Authorities".
(
Start - Run/Search - certlm.msc)
2. Error:
@sessionlog@
. 2017-02-06 17:02:40.025 Certificate failed to verify against Windows certificate store: Error: 80092013, Chain index: 0, Element index: 0
Check:
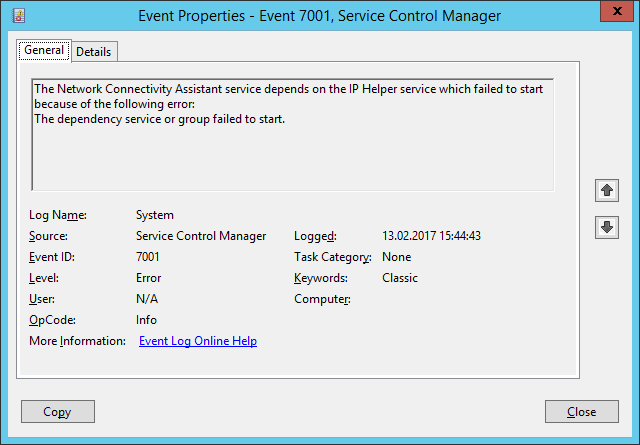
Event Viewer (Local) - Windows Logs - System
for the Errors:
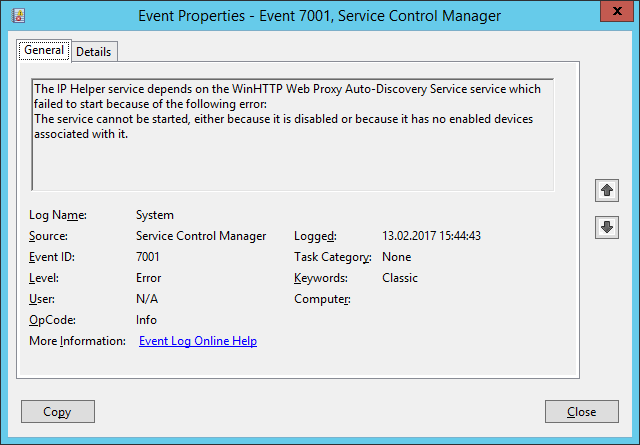
The IP Helper service depends on the WinHTTP Web Proxy Auto-Discovery Service service which failed to start because of the following error:
The service cannot be started, either because it is disabled or because it has no enabled devices associated with it.
The Network Connectivity Assistant service depends on the IP Helper service which failed to start because of the following error:
The dependency service or group failed to start.
If there is one, turn on (set to
Automatic) and then start the service:
Service name: WinHttpAutoProxySvc
Display name: WinHTTP Web Proxy Auto-Discovery Service
Description: WinHTTP implements the client HTTP stack and provides developers with a Win32 API and COM Automation component for sending HTTP requests and receiving responses. In addition, WinHTTP provides support for auto-discovering a proxy configuration via its implementation of the Web Proxy Auto-Discovery (WPAD) protocol.
After that, start the service:
Service name: iphlpsvc
Display name: IP Helper
Description: Provides tunnel connectivity using IPv6 transition technologies (6to4, ISATAP, Port Proxy, and Teredo), and IP-HTTPS. If this service is stopped, the computer will not have the enhanced connectivity benefits that these technologies offer.
You in my case it start working!
You will get this line in WinSCP logs for success:
. 2017-02-13 15:47:41.487 Certificate verified against Windows certificate store
Last edited by Makc666 on 2017-02-14 13:19; edited 4 times in total