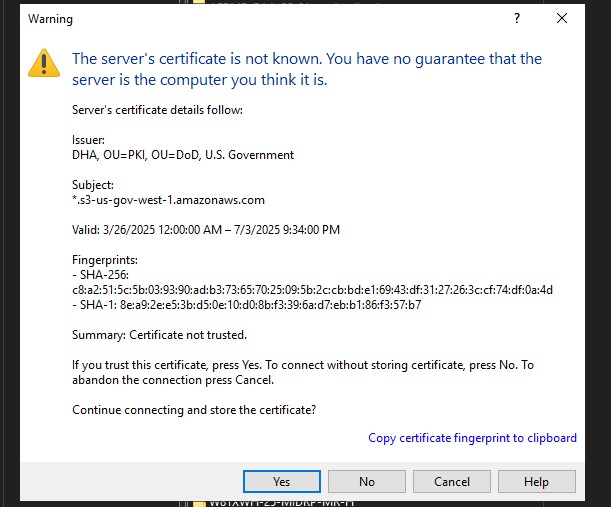
Incessant certificate warnings
I've dug around the net and I haven't found anything that applies to bypass that warning using the GUI (vs .NET code).
-certificate * looked promising in the .ini (to be narrowed down if that worked), but made no difference, nor did I find anything applicable or germane in the Raw Settings for that session.
Any way out of this? This has put us at a bit of a standstill. Thanks!
I ran the log in debug and below is all that it had re certificates.
. 2025-06-13 16:05:58.130 Doing SSL negotiation. . 2025-06-13 16:05:58.280 ssl: Verify callback @ 2 => 20 . 2025-06-13 16:05:58.280 ssl: Verify failures |= 8 => 8 . 2025-06-13 16:05:58.295 Chain depth: 3 . 2025-06-13 16:05:58.295 Identity match for '': bad . 2025-06-13 16:05:58.295 Identity match for '': bad . 2025-06-13 16:05:58.295 Identity match for '': bad . 2025-06-13 16:05:58.295 ssl: Match common name '*.s3-us-gov-west-1.amazonaws.com' against 's3.us-gov-west-1.amazonaws.com' . 2025-06-13 16:05:58.295 ssl: Match common name 's3-us-gov-west-1.amazonaws.com' against 's3.us-gov-west-1.amazonaws.com' . 2025-06-13 16:05:58.295 ssl: Match common name '*.s3.us-gov-west-1.amazonaws.com' against 's3.us-gov-west-1.amazonaws.com' . 2025-06-13 16:05:58.295 ssl: Match common name 's3.us-gov-west-1.amazonaws.com' against 's3.us-gov-west-1.amazonaws.com' . 2025-06-13 16:05:58.295 Identity match for 's3.us-gov-west-1.amazonaws.com': good . 2025-06-13 16:05:58.295 Verifying certificate for "*.s3-us-gov-west-1.amazonaws.com" with fingerprint 4e:80:b7:a9:31:3f:4d:55:ee:7e:fb:f8:85:a6:e0:e7:09:a5:9c:2f:26:ed:c7:2f:c7:54:8d:c6:8d:ff:e7:7b and 08 failures . 2025-06-13 16:05:58.418 Certificate verified against Windows certificate store