This is an old revision of the document!
Authentication Page (Advanced Site Settings dialog)
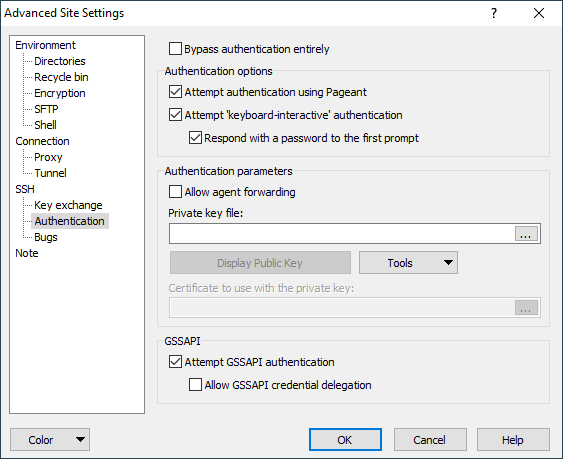
The Authentication page on the Advanced Site Settings dialog allows you to configure authentication options of SSH protocol.
Advertisement
To reveal this page you need to select SCP or SFTP file protocol on Login dialog.
Refer to documentation of page sections:
Bypassing Authentication
In SSH-2, it is possible to establish a connection without using SSH’s mechanisms to identify or authenticate oneself to the server. Some servers may prefer to handle authentication in the data channel, for instance, or may simply require no authentication whatsoever.
Advertisement
By default, WinSCP assumes the server requires authentication (most do), and thus must provide a username. If you find you are getting unwanted username prompts, you could try checking Bypass authentication entirely.
This option only affects SSH-2 connections. SSH-1 connections always require an authentication step.1
Authentication Options
Attempt Authentication Using Pageant
If this option is enabled, then WinSCP will look for Pageant and attempt to authenticate with any suitable public keys Pageant currently holds.
This behavior is almost always desirable, and is therefore enabled by default. In rare cases you might need to turn it off in order to force authentication by some non-public-key method such as passwords.1
Learn how to use the Pageant (PuTTY’s SSH authentication agent) application for public key authentication.
Attempt TIS or CryptoCard authentication
TIS and CryptoCard authentication are (despite their names) generic forms of simple challenge/response authentication available in SSH-1 only. You might use them if you were using S/Key one-time passwords, for example, or if you had a physical security token that generated responses to authentication challenges. They can even be used to prompt for simple passwords.
With this switch enabled, WinSCP will attempt these forms of authentication if the server is willing to try them. You will be presented with a challenge string (which may be different every time) and must supply the correct response in order to log in. If your server supports this, you should talk to your system administrator about precisely what form these challenges and responses take.1
Attempt keyboard-interactive authentication
The SSH-2 equivalent of TIS authentication is called ‘keyboard-interactive’. It is a flexible authentication method using an arbitrary sequence of requests and responses; so it is not only useful for challenge/response mechanisms such as S/Key, but it can also be used for (for example) asking the user for a new password when the old one has expired.1
WinSCP leaves this option enabled by default, but supplies a switch to turn it off in case you should have trouble with it. If your server uses keyboard-interactive authentication to ask for your password only, and you wish to allow WinSCP to reply with password entered on Login dialog, tick Respond with password to the first prompt.
Authentication Parameters
Allow agent forwarding
This option allows the SSH server to open forwarded connections back to your local copy of Pageant. If you are not running Pageant, this option will do nothing. Learn more about agent forwarding.
Advertisement
Private key file
Use the Private key file box to specify local path to your private key file if you are going to use public key authentication. The file must be in PuTTY format. If the private key is passphrase-protected, you will be prompted for passphrase once the authentication begins. If you have your private keys loaded into Pageant, leave the box blank, unless you want to ensure that only that particular key is used for authentication.
The passphase cannot be entered in advance on Login dialog and thus it cannot be saved to site. If you need to login to server automatically without prompt, generate key without passphrase. Use this method carefully and only under special circumstances.
If you select a key file in a different format (OpenSSH or ssh.com), WinSCP will offer you to convert the key to PuTTY format. This feature is available only in the latest beta release.
GSSAPI
Attempt GSSAPI authentication
The switch controls the use of GSSAPI authentication. This is a mechanism which delegates the authentication exchange to a library elsewhere on the client machine, which in principle can authenticate in many different ways but in practice is usually used with the Kerberos single sign-on protocol.
GSSAPI is only available in the SSH-2 protocol.
If the option is disabled, GSSAPI will not be attempted at all and the rest of this panel is unused. If it is enabled, GSSAPI authentication will be attempted, and (typically) if your client machine has valid Kerberos credentials loaded, then WinSCP should be able to authenticate automatically to servers that support Kerberos login.
Allow GSSAPI credential delegation
GSSAPI credential delegation is a mechanism for passing on your Kerberos (or other) identity to the session on the SSH server. If you enable this option, then not only will WinSCP be able to log in automatically to a server that accepts your Kerberos credentials, but also you will be able to connect out from that server to other Kerberos-supporting services and use the same credentials just as automatically.
This option is the Kerberos analogue of SSH agent forwarding.
Note that, like SSH agent forwarding, there is a security implication in the use of this option: the administrator of the server you connect to, or anyone else who has cracked the administrator account on that server, could fake your identity when connecting to further Kerberos-supporting services. However, Kerberos sites are typically run by a central authority, so the administrator of one server is likely to already have access to the other services too; so this would typically be less of a risk than SSH agent forwarding.1
Further Reading
Read more about Login dialog and Advanced Site Settings dialog.
Advertisement
- The text is copy of PuTTY User Manual or was inspired by it.Back