This is an old revision of the document!
SSH Page (Advanced Site Settings dialog)
The SSH page on the Advanced Site Settings dialog allows you to configure options of SSH protocol and encryption.
Advertisement
To reveal this page you need to select SCP or SFTP file protocol on Login dialog.
More SSH options are available on subpages:
- Key exchange (key exchange and reexchange options)
- Authentication (advanced authentication options)
- Bugs (detections of known bugs in SSH servers)
Refer to documentation of page sections:
Protocol Options
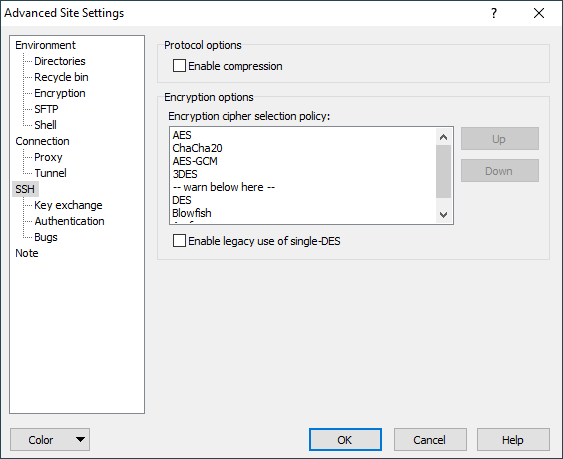
The Enable compression checkbox enables data compression in the SSH connection: data sent by the server is compressed before sending, and decompressed at the client end.
The Preferred SSH protocol version selection allows you to select whether you would like to use SSH protocol version 2 or legacy version 1, and whether to permit falling back to the other version. If you select 2 only or 1 only here, WinSCP will only connect if the server you connect to offers the SSH protocol version you have specified. With the settings 2 and 1, WinSCP will attempt to use protocol 1 if the server you connect to does not offer protocol 2, and vice versa.
You should normally leave this at the default, 2 only. The older SSH-1 protocol is no longer developed, has many known cryptographic weaknesses, and is generally not considered to be secure. If you permit use of SSH-1 by selecting 2 instead of 2 only, an active attacker can force downgrade to SSH-1 even if the server you’re connecting to supports SSH-2.1
Advertisement
You can see actually used protocol version on Server and Protocol Information Dialog.
Encryption Options
WinSCP supports a variety of different encryption algorithms, and allows you to choose which one you prefer to use. You can do this by dragging the algorithms up and down in the list box (or moving them using the Up and Down buttons) to specify a preference order. When you make an SSH connection, WinSCP will search down the list from the top until it finds an algorithm supported by the server, and then use that.
WinSCP currently supports the following algorithms:
- AES (Rijndael) - 256, 192, or 128-bit SDCTR or CBC
- Arcfour (RC4) - 256 or 128-bit stream cipher
- Blowfish - 256-bit SDCTR or 128-bit CBC
- Triple-DES - 168-bit SDCTR or CBC
- Single-DES - 56-bit CBC (see below for SSH-2)
If the algorithm WinSCP finds is below the warn below here line, you will see a warning box when you make the connection:
The first cipher supported by the server is single-DES, which is below the configured warning threshold.
Do you want to continue with this connection?
This warns you that the first available encryption is not a very secure one. Typically you would put the warn below here line between the encryptions you consider secure and the ones you consider substandard. By default, WinSCP supplies a preference order intended to reflect a reasonable preference in terms of security and speed.
In SSH-2, the encryption algorithm is negotiated independently for each direction of the connection, although WinSCP does not support separate configuration of the preference orders. As a result you may get two warnings similar to the one above, possibly with different encryptions.
Single-DES is not recommended in the SSH-2 protocol standards, but one or two server implementations do support it. WinSCP can use single-DES to interoperate with these servers if you enable the Enable legacy use of single-DES in SSH-2 option; by default this is disabled and WinSCP will stick to recommended ciphers.1
You can see actually used encryption algorithm on Server and Protocol Information Dialog.
Further Reading
Read more about Login dialog and Advanced Site Settings dialog.
- The text is copy of PuTTY User Manual or was inspired by it.Back